The world is changing quickly and so are the technologies that militaries rely on. As trends in technology progress, defence professionals must adapt to the changing landscape.
To stay atop military priorities, Hexagon considered the defence landscape and researched how technology can benefit the teams that use it. Some of the variables include:
- Threats: State actors, non-state actors or economic conditions
- Opportunities: Civilian knowledge or collaborative workspaces
- Directions: Alternating between peacekeeping missions, defence changes and public sentiments
- Updating older technologies past their intended life and making use of other industry tools
Considering these variables, we made a list of the top 10 trends to look out for in the defence industry that are in various stages of adoption and maturity. To read the full list, you can download our white paper here. For a sneak peek of two of the trends, read below.
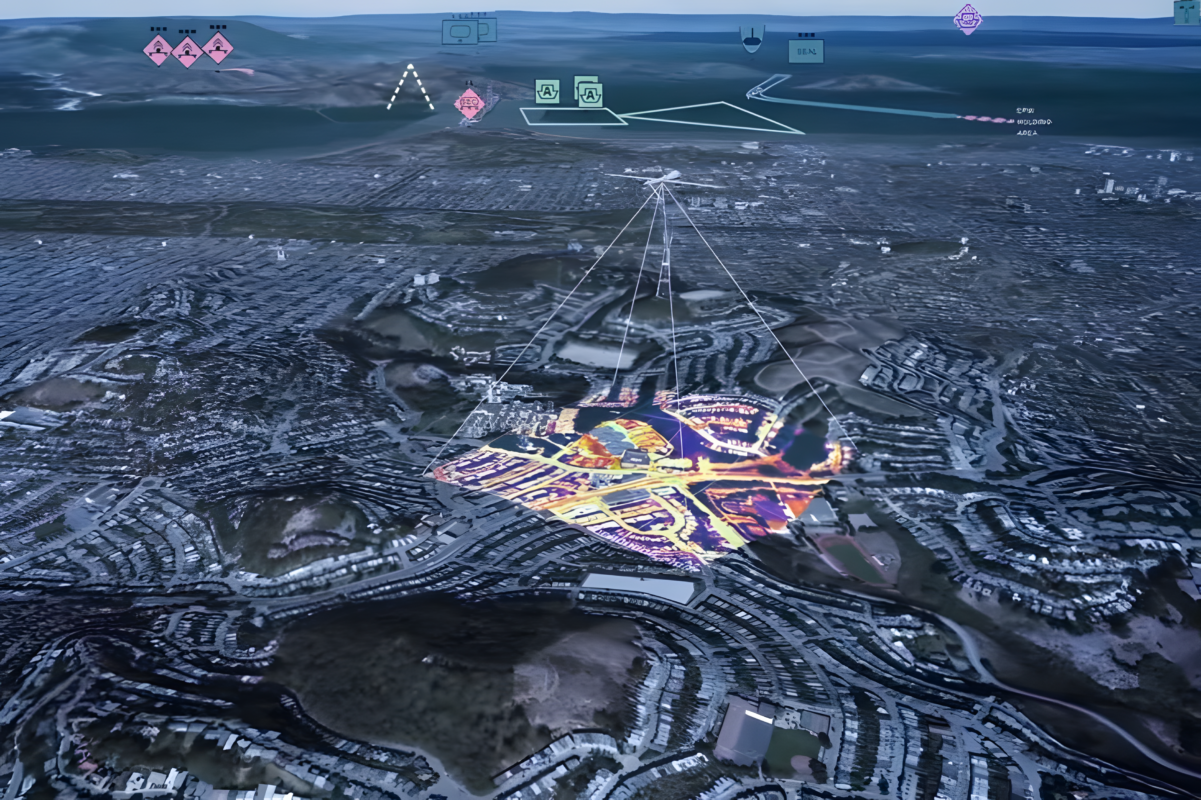
More sensor integrations and better data analysis for ISR systems
Intelligence, surveillance and reconnaissance (ISR) systems provide real-time intelligence and a common operational picture for their users. With technology progress, ISR systems are expected to have faster reactions, more sensors to collect data, provide a wider range of products to consumers and have greater analysis capabilities. IoT capabilities and sensor numbers are increasing, and in defence that data will be used to focus on specific information like the position location information of individual service personnel. This data will be used strategically, but to be useful in real-time, it often needs to have already been analysed with the results ready to be presented. Hexagon provides capabilities that can streamline and automate the ISR task management process and allow rapid, cloud-based intelligence sharing.
Securing mission-critical data with firewalls and encryption
Data security is the main concern for defence trends. Everyone has more connectivity and sharing capabilities than ever before. This presents a higher potential for critical data leaks and security weaknesses. While not all intrusions will be intentionally malicious, cyberattacks, missent emails and any other breaches need to be and can be minimised with technology and processes. Integrating each level of data protection can help, for file level, data level or level. Data security can be fine-tuned and implemented in a way to encrypt file-level data or restrict certain users to specific data, such as distinct geographic areas. Grey war zones happen when actors try to get advantage over an adversary through non-combat methods. These have increased with digital data and can happen through methods such as cyberattacks, espionage, disinformation on social media or unintentionally through spread of misinformation. Data and information should be traceable and assured as far as possible.
Conclusion
Change is a guarantee as the digital world moves forward. You might pick change, or it might be forced on you, but everyone needs to be prepared for it to happen. The change of pace for the defence landscape is only destined to increase. Militaries and their technology providers must be prepared to fully connect and leverage data for faster, more effective information delivery and use.
Read the white paper to learn about all 10 defence trends here.












