The dramatic geopolitical changes in 2022 have caused alarm among countries and caused more attention to be paid to defence and security vulnerabilities. Previously considered secure, borders and shorelines are susceptible to criminal and terrorist activity, exposing essential economic infrastructure and strategic sites to hostile attacks.
Security measures that previously focused on preventing smugglers by regulating the movement of people and vehicles across borders now aim to stem waves of migrants and the trafficking of illegal substances using submarines and unmanned vehicles, or drones. The new world order exposes more nations to terror threats, either cross-border attacks or proxy states supporting terror cells inside those countries. This new reality demands the establishment of broader, more persistent, and highly responsive border protection, integrating existing capabilities with new concepts and technologies to deal with these new challenges.
Nevertheless, the basics of border protection missions remain unchanged: as a nation’s perimeter defines its sovereign area, the borderline should be monitored to block unauthorised air, land, or marine traffic, limit all movements to defined passages, and employ security forces to respond to any violation of secured areas. This task is simple to define, but given the variety of threats, it is difficult to implement. In this article, we review some of the challenges and technological solutions made available with modern technology.
Foliage Penetration
In the past, ground surveillance radars were often used to cover large areas. Based on Doppler effect filtering, these radars were tuned to detect vehicles at tens of kilometres and humans at distances of a few kilometres away, alert additional observation means to identify targets and direct security forces to close in on the suspected threats and apprehend them as they attempt to cross the border. The war in Ukraine has highlighted for example the difficulty of sensors in penetrating dense foliage.
While airborne sensors such as synthetic aperture radars (SAR) effectively penetrate foliage, detecting movement in such an environment is more difficult. While most ground surveillance radars operate well in open terrain, they are ill-equipped to detect targets or movements covered by dense foliage, such as forests, shrubs, plantations, or jungles. Low-flying aircraft or small and slow Unmanned Aerial Vehicles (UAVs) also pose different challenges for radars.
Legacy sensors are less likely to detect such targets and, therefore, need assistance in adapting algorithms and filters. Modern Foliage-Penetrating (FOLPEN) radars provide some solutions for detection in vegetated terrain; such radars employ ground-based or overhead sensors from aircraft or drones, enabling radars to penetrate dozens of metres deep into densely covered terrain. To fill this gap, Israel’s radar specialist Elta Systems has added the L-band ELM2112FP to its family of ground surveillance radars. This model can detect a human at a distance of 2.5 km and a vehicle from 5 km, even when such targets are tens of metres inside a dense forest.
Counter-Unmanned Aerial Vehicle (C-UAV)
Drones present a challenge to radar surveillance as they are often unseen by radars due to their much smaller dimensions, low-altitude flight, and slow speed. To cope with the challenge, some ground surveillance radars have evolved to meet the challenge posed by UAVs.
For example, Leonardo’s TMMR is designed to detect low, slow, small, fast, and high manoeuvring targets. Typical applications include: C-UAV; Very Short-Range Air-Defence (VSHORAD); Counter-Rocket Artillery Mortar (C-RAM); airport/critical infrastructure surveillance; air surveillance gap filler; vehicle protection; and battlefield protection.
Another relatively new radar solution adapted to border security and C-UAV is Weibel’s XENTA-C, an X-band drone detection radar that monitors drone activity across borders and other perimeters. As a compact radar, it can be mounted on ground-based installations, packed in a containerised solution for deployment, or mounted on small land-based vehicles, such as pick-up trucks, for rapid deployment as a gap-filler on a forward location.
As a C-UAV radar, it effectively detects and classifies drones and delivers tracking info to control centres, frequency jammers, and optronic systems via integration into a command and control (C2) system. As a Doppler radar, it detects the target’s movement. When operated against drones, it can detect both the drone’s movement and the rotor blades’ rotation. Combining both signals is what provides a high probability of detection.

Credit: Weibel
Wide-Area Surveillance
The development of advanced optronic cameras with multi-megapixel sensors has enabled designers to introduce new concepts of optronics systems providing Wide-Area Motion Imagery (WAMI), using high-resolution optronic cameras to take frequent time-lapse imagery or continuous video of a wide area, enabling analysts to look back in time for forensic investigation of certain events. WAMI represents a new approach to intelligence, surveillance, and reconnaissance that employs an elevated wide-area surveillance sensor system to image, detect, and track every vehicle, every moving dismount, over a designated area of several kilometres in diameter. Typical systems used on light aircraft or drones can cover areas from 2 to 16 km2 with high-resolution imagery, supporting analysts with windows of interest of specific locations or tracking movements of vehicles or personnel throughout the covered area.
Typical WAMI payloads from LOGOS allow operators to track multiple targets moving simultaneously in different directions, a popular evasion technique for terrorists and smugglers. The system records and archives everything it sees, allowing users to conduct real-time and forensic analysis, uncovering critical ties between people, places, and vehicles, and identifying patterns of behaviour that might otherwise have been missed. WAMI systems can be mounted on various platforms, including aerostats and tethered UAVs, maintaining persistent surveillance of a city-size area points of interest for weeks at a time. As part of such surveillance, operators can establish ‘watch boxes’ over specific areas, to trigger automated tripwire alerts.
Today’s WAMI payloads are not as bulky and heavy as previous systems. Using payloads mounted on small, tethered Class 1 drones, imagery covering days, or weeks, can be analysed to gain insights into patterns of life that help uncover hidden relationships between various actors, locations, and events in the area under surveillance.

Autonomy for Timely Response
Having an all-seeing eye in the sky does not mean border guards can react quickly enough for effective response, especially when long borders are secured by small, widely dispersed teams. When securing a ‘hot’ border, where hostile activities are expected, and guards do not ask many questions before opening fire, long-range precision weapons will likely be an effective response and deterrent. However, various robotic measures can be employed on more peaceful borders to contain a situation and hold border trespassers until guards arrive at the scene.
Originally used in remotely-operated mode, Unmanned Ground Vehicles (UGV) such as IAI’s REX MK2 are today used semi-autonomously. The vehicles are equipped with various sensors, providing them a limited degree of autonomy to respond to situations they may encounter. Other equipment may include laser scanners that can sweep the border fence in search of changes – new openings, appearance of new objects that could indicate the placement of mines or roadside IEDs, gunshot detectors to report on possible engagement by hostiles, and a weapon station providing cameras and weapons to engage targets on demand and under the operator’s control. Such UGVs can perform slow but continuous patrols along a borderline without requiring human guards to be present on these missions.

Drones can deploy even faster from pre-positioned sites placed along the fence or in remote operating locations placed along a long borderline. Different missions may require specific solutions. The Israeli company SPEAR UAV has developed the Ninox system.
Triggered by a smart fence, radar, cameras, or other means, the Ninox system deploys a tube-launched drone in response to an alert, enabling border protection teams to respond quickly and effectively to real-time threats. Designed as an affordable sensor or weapon, Ninox is cost-effective and compact, enabling the deployment of multiple units along a border fence or on moving patrol vehicles, enabling the operator to direct the payload weighing up to 0.5 kg in wind speeds of up to 10.3 m/s (20 knots), and without requiring drone piloting skills.

Credit: Spear UAV
A different concept of prepositioned drones includes the Easy Guard ground station that provides a smart, independent drone hangar for take-off, landing, and charging. Drones can be operated in tethered mode or free flight, as needed. It features an automated roof opening and closing and multiple sensors and cameras for environmental monitoring and situational awareness. Such units can be prepositioned at unattended remote sites, mounted on patrol vehicles or unmanned vehicles, providing security forces with an effective response to emergency situations requiring an overhead lookout over a given area.

Credit: Tamir Eshel
System integration
Performing the border protection role requires the combination of all different elements into a comprehensive C2 system, depicting the broad situational picture and assigning specific tasks for the different teams performing routine patrols or responding to alerts. Like military C2 systems, border protection and management systems also employ sophisticated information systems to process and correlate the input from multiple sensors and combine those feeds into knowledge, refining it for the commanders and presenting subsets of the relevant information to the response teams tasked with to seeking, intercepting, arresting or elimination of specific targets. In some cases, responses require the activation of other systems, including C-UAV, anti-aircraft, or robotic guards.
A typical system is Anduril’s LATICCE, a C2 system that creates a shared understanding of the scene in real time by autonomously passing data from all sensors and data sources, and then refining the information into an intelligent common operating picture. The system uses technologies such as sensor fusion, computer vision, edge computing, machine learning, and artificial intelligence to detect, track, and classify every object of interest in an operator’s vicinity. The system’s user interface (UI) allows users to visualise and interact with thousands of sensors and effectors in a single UI and seamlessly scale from tactical to strategic views.
Another example, is the NIDAR C2 intelligent border surveillance system from British company MRASS, designed to provide autonomous border and perimeter surveillance solutions. This system’s AI-powered NIDAR Core employs an Internet of Things (IoT) approach, using connected electronic sensors and devices to create the situational map for operational decisions. According to MRASS, the system developer, NIDAR Core is a hybrid intelligence solution that exploits expertise through operational logic.
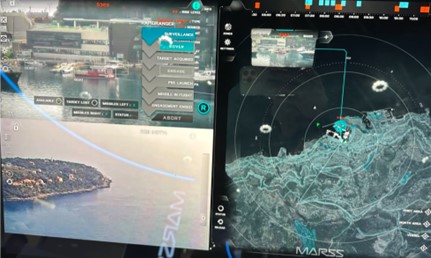
Credit: Tamir Eshel
Summary
Collectively, these aspects are integrated into a single situational awareness picture to facilitate efficient border protection operations. Such systems should interface with new and legacy systems and sensors, to integrate all the country’s relevant capabilities under one interface, from intelligence gathering and analysis, through mission planning, to the countering of asymmetric threats on land, at sea, and in the air, to form a layered integrated surveillance and defence capability that detects, identifies, alerts, and responds to current and evolving cross-border threats.
Tamir Eshel




![Is Cellular Connectivity the Key to UAV and UGV Battlefield Dominance? Is Cellular Connectivity the Key to UAV and UGV Battlefield Dominance? By Yoav Amitai, CEO, [Copyright: Elsight]](https://euro-sd.com/wp-content/uploads/2025/08/Elsight-Article-Image-Is-Cellular-Connectivity-the-key-to-UAV-218x150.jpg)

![Are you deceiving me? A dummy Sherman tank, of the type used by FUSAG. [US National Archives]](https://euro-sd.com/wp-content/uploads/2025/05/Dummy-Sherman-tank_US-National-Archives-Kopie-218x150.jpg)





