The escort jamming mission is a staple of airborne electronic warfare, but it will grow in complexity as new tactics and levels of connectivity come to the fore.
At first blush, escort jamming seems a relatively simple task. It involves the transmission of jamming signals into red force ground-based air surveillance and Fire Control/Ground-Controlled Interception (FC/GCI) radars. This helps protect blue force aircraft as they perform their missions in contested airspace. Red force radars will be the eyes of an Integrated Air Defence System (IADS) protecting all, or a large part, of a nation’s airspace.
They may protect red force airspace at operational and tactical levels during land operations. These radars will be networked with deployed Surface-to-Air Missile (SAM) and Anti-Aircraft Artillery (AAA) systems. The key tenet of ground-based air defence is to provide layered hard kill at ever-expanding ranges and altitudes. FC/GCI radars provide target location information to red force fighters and are linked to GCI centres. These centres receive imagery from the assorted radars protecting red force airspace. These disparate radar pictures are merged into a recognised air picture of the airspace under the centre’s control. That way, threats can be detected, identified, tracked and then engaged with either SAMs, AAA or fighters.

Credit: Ukraine Weapons Tracker, via Twitter
Blinding red force radar is paramount and is achieved through kinetic attack against the radars using ordnance or through electronic attack. The latter can take the form of conventional jamming. Radars are inundated with electromagnetic noise significantly degrading their performance. An analogy of this is when a car goes under a high-tension power line and the driver hears static noise on their radio. This noise may drown out the programme they were listening to.
Alternatively, red force radar signals may be sampled, subtly altered and retransmitted back to the radar, a tactic known as deception jamming. For example, the incoming radar signal maybe manipulated to fool the radar into thinking there are more aircraft are in the sky than there really are. This ruse will cause confusion at the GCI centres as the radars will be sharing authentic-looking, but false, information.
Jamming signals may also transmit malicious computer code into the radar. Most contemporary radars are digital systems using software to generate and interpret their signals and control their operation. Malicious code can be transmitted into communications antennas or potentially even the radar antenna to infect the radar. Alternatively, as the radars are likely to be networked, the code may spread across the communications links connecting the radars to the GCI. The code may also infect networked SAM batteries and AAA systems. Command and control software the IADs relies on to facilitate operations may be similarly affected. Like deception jamming, it may not be immediately obvious to red force air defenders that their systems have been infected.
Today’s and tomorrow’s escort jammers may perform a combination of these tactics while protecting other friendly aircraft. Escort jamming is so-called because it accompanies packages of aircraft while they perform their missions in contested airspace. This is distinct from aircraft self-protection which will use jamming techniques chiefly to protect an individual platform. Escort jamming requires specialist equipment usually in the form of a jamming pod. The pod needs to house electrical equipment generating significant levels of jamming power to protect blue force aircraft over a large area. Aircraft self-protection jammers do not need to generate equivalent power levels because they have a far smaller area around the plane to defend. Some escort jamming pods use a ram air turbine, a small propeller positioned at the front of the pod. The turbine rotates at speed as the aircraft flies, thereby generating the requisite power levels. This avoids having to use the aircraft’s own engines to generate this power which risks depriving the aircraft’s other electrical systems.
Tactics
Escort jammers typically provide jamming support beyond the detection range of the red force’s radars. Hopefully, this will avoid the aircraft carrying the jammer being detected by hostile radar. Protecting escort jamming aircraft is paramount as once these are destroyed, the blue force loses escort jamming coverage.
To understand how the escort jammer’s task works, we need to talk about radar signals which have main lobes and sidelobes. As figure 1 shows, these look like petals of a flower fanning out either side above and below of the main lobe. The main lobe is the most powerful part of the signal and is in effect the boresight where the radar points its signal to detect and track targets. Circa 80% of a radar’s transmitted power is contained in the main lobe. As this is where the most of the radar’s power is going, a jammer needs significant power to jam this signal.
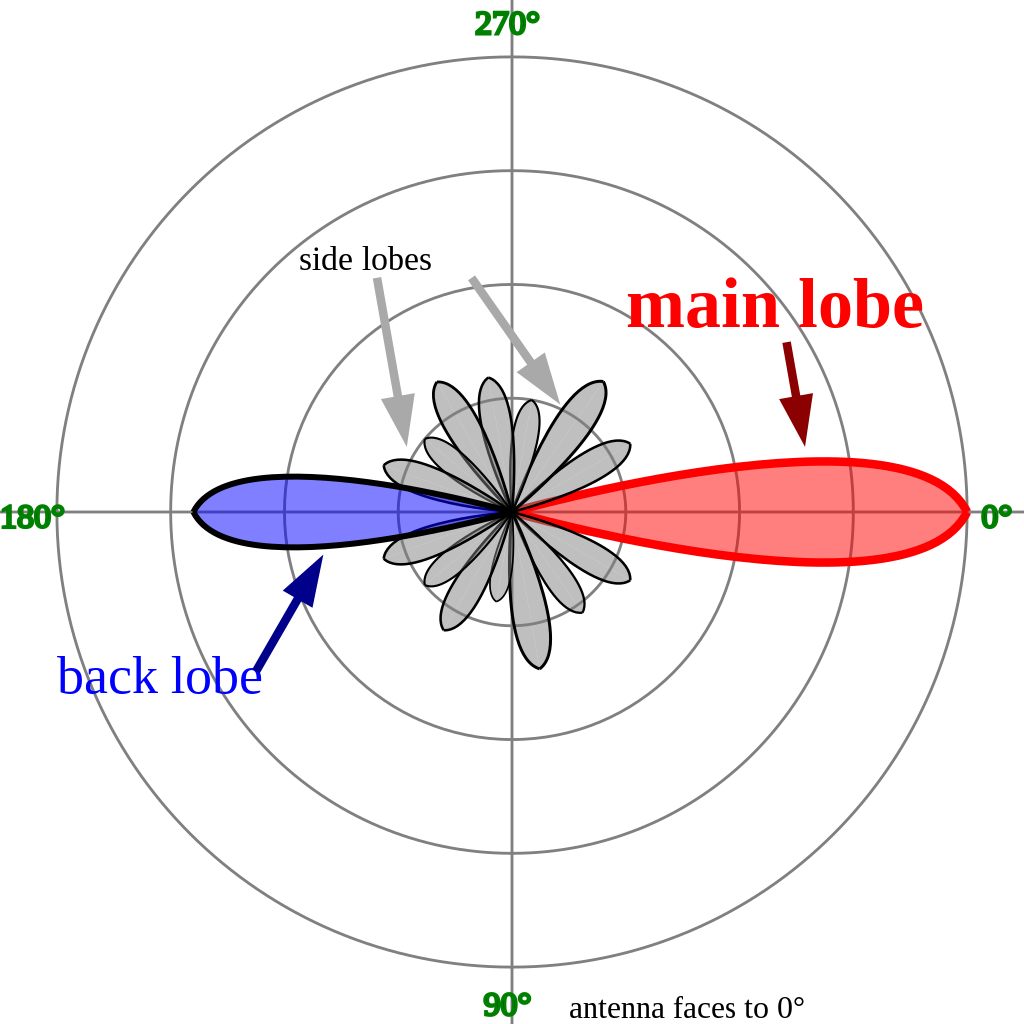
Credit: Timothy Truckle
The strength of the jammer’s signal must eclipse that of the radar’s by the time the jamming signal reaches the radar’s antenna. Signal strength is measured in decibels (dB). Let us consider this hypothetical, and highly unlikely, scenario. The red force has an antiquated FuMG-62D Würzburg FC/GCI radar. The FuMG-62D was widely used by the Luftwaffe (German Air Force) during the Second World War. The blue force plans to jam this radar using an ITT/L3 Harris ALQ-99 airborne jamming pod carried by one of its fighters.
The FuMG-62D and ALQ-99 both have details regarding their signal strengths available in the public domain. As one can imagine, such details can be closely guarded secrets. However, the FuMG-62D is now beyond obsolete and the ALQ-99 is in its twilight years.
Let us suppose the radar is transmitting on a frequency of 560 MHz and, for the purpose of this discussion, that the ALQ-99 can detect and attack such transmissions. The aircraft carrying the pod is 30 km (16.2 NM) from the radar and in its main lobe. The radar is transmitting a 7 kW signal while the AN/ALQ-99 transmits a 6.8 kW jamming signal. The efficacy of the jammer is not merely a function of how powerful the jamming signal it transmits into the radar is. A host of other factors come into play, such as the gain of the radar and the jammer. In essence, gain is the level of signal concentration the radar or jammer can direct onto its target. The power levels of the outgoing radar and jamming signals also make a difference, alongside other factors like the weather and electromagnetic activity in the atmosphere. We want to reduce the range at which the red force radar detects the blue force aircraft with the jammer, and we are in luck. In this case, the jammer’s signal strength reduces the radar’s signal strength to the extent that it cannot detect targets beyond a 14 km (7.6 NM) range.
Ideally, we want to keep our aircraft carrying the jammer beyond the 30 km (16.2 NM) maximum range of the FuMG-62D while ensuring the FuMG-62D cannot detect other blue force aircraft flying nearer to the radar. Let us suppose we have our jamming pod aircraft at a range of 60 km (32.4 NM) from the FuMG-62D. We want to protect other blue force aircraft that must fly within 10.8nm (20km) of the offending radar. The jammer is notably further away in this example, but thanks to its signal strength, it still reduces the radar’s detection range to 14.5 km (7.8 NM). Blue force aircraft can fly within the radar’s detection range, but to remain undetected thanks to the jamming. An even safer option for the jammer aircraft is to attack the radar by transmitting the jamming signal into its sidelobes. Sidelobes reduce in strength as they fan out from the main beam and cannot detect targets at the same range, because they are not strong enough.
Dedicated Platforms
A few nations maintain fleets of combat aircraft dedicated to detecting, identifying and jamming radars. The first such aircraft appeared during the Second World War. The Royal Air Force’s Bomber Command maintained a dedicated electronic warfare unit called 100 Group. As the Command waged its war against Axis strategic targets in the European theatre of operations, 100 Group gave invaluable support. It used specially adapted light, medium and heavy bombers. These were tricked up with Electronic Support Measures (ESMs) and Electronic Countermeasures (ECMs). The ESMs would seek out Luftwaffe airborne and ground-based radars, surface-to-air/air-to-surface radio communications and radio navigation systems. These emitters would then be blasted with torrents of electromagnetic noise using onboard ECMs. Powerful ground-based ECMs in the United Kingdom gave similar support hundreds of nautical miles into occupied Europe.
The concept of dedicated EW aircraft supporting strike packages of combat aircraft was further refined in the Cold War, notably during the United States’ involvement in the Vietnam War between 1965 and 1975. The US Navy began its ‘Iron Hand’ missions in 1965. Iron Hand used navy aircraft equipped with AGM-45 Shrike variant anti-radar missiles.
Shrike was developed by the US Navy’s Naval Weapons Centre. Packages of Iron Hand aircraft included Douglas A-4 Skyhawk and A-3 Skywarrior series combat aircraft. These planes were escorted by Vought F-8 Crusader variant fighters. The missions were dedicated to finding and destroying radar-guided SAM and AAA batteries the Soviet Union had supplied to its North Vietnamese allies. Radar Warning Receivers (RWRs) would advise A-3 and A-4 pilots that a hostile radar was nearby and active. AGM-45s would then be launched and home in on the hostile radar signal, destroying the antenna. A variant of the mission, known as ‘Wild Weasel’, was adopted by the US Air Force (USAF), commencing the same year as Iron Hand.
The Wild Weasel mission continues in the USAF today. Dedicated General Dynamics/Lockheed Martin F-16CJ Viper Weasel combat aircraft are armed with Texas Instruments/Raytheon AGM-88 HARM (High Speed Anti-Radiation Missile) variant weapons and Raytheon’s AN/ASQ-213 HARM Targeting System (HTS). The latter hunts for hostile radar signals. When discovered, the aircraft launches the HARM which, like the AGM-45, uses these signals to home in on the hostile radar, destroying it.

Credit: US Navy
The US Navy has continued to refine its Iron Hand capabilities. In 1971, the force introduced the Northrop Grumman EA-6B Prowler, equipped with AN/ALQ-99 jammers and deploying the AGM-88. The Prowler had a long career until its eventual replacement from 2009 by Boeing’s E/A-18G Growler. For now, the Growler deploys the AN/ALQ-99. The AN/ALQ-99 is being progressively replaced by the US Navy’s low-, mid- and mid-band extended Next Generation Jammer (NGJ). The first of these, Raytheon’s AN/ALQ-249, has already entered service and detects and jams radar threats across frequencies of 2-6 GHz. The low-band NGJ will cover wavebands of 500 MHz to 2 GHz and is awaiting contract award. Reports in May said the navy is looking to extend the AN/ALQ-249 to cover higher frequencies, circa 18 GHz. The force had originally planned to procure a separate high-band jammer, but this now appears to have been abandoned. Extending the AN/ALQ-249’s capabilities would be arguably more cost-effective than procuring a third NGJ variant.
The US’ European North Atlantic Treaty Organisation (NATO) partners are receiving new escort jamming capabilities in the form of the Luftwaffe’s Eurofighter Typhoon-EW electronic warfare jet. The Typhoon-EW replaces the Luftwaffe’s legacy Panavia Tornado-ECR suppression/destruction of enemy air defence aircraft. During the 2023 Association of Old Crows’ (AOC) Electronic Warfare conference in Bonn, western Germany held on 15-16 May, officials close to the programme told the author that the type of escort jammers these aircraft will carry are yet to be determined. Nonetheless, the Typhoon-EW will be spoiled for choice. Escort jammers are available from Elettronica (EDGE), Hensoldt (Kalætron), Indra (ALQ-500P), Israel Aerospace Industries (EL/L-8222SB Scorpius), Leonardo (Common Jamming Pod), Northrop Grumman (AN/ALQ-131), Rafael Advanced Defence Systems (SkyShield) and Saab (Arexis).

Credit: Airbus
Meanwhile, the European Union is advancing its Airborne Electronic Attack (AEA) initiative, one of the European Defence Agency’s Permanent Structured Cooperation (PESCO) programmes. It would not be surprising if the German government selects a podded version of the jamming technology developed via the AEA programme. This would underscore Germany’s ongoing commitment to the European defence industry writ large. It would also avoid the country procuring escort jammers for the Typhoon-EW from the US. Lawmakers in Washington DC may be prepared to supply technology like the AN/ALQ-249 to Germany, much like it has to Australia. Nonetheless, this could come with caveats covering access to advanced signal processing and jamming technology used by the US Navy in their pods. Others could include restrictions on when and where the pods are used operationally. As Hensoldt is already involved in the AEA initiative, any procurement of the technology yielded under AEA would benefit Germany.
While Germany is buying a dedicated jamming aircraft in the guise of the Typhoon-EW, escort jamming pods represent a cost-effective way that air forces can deploy powerful EW tools without needing dedicated platforms. Several pods can be purchased and moved between aircraft as and when required. The author’s records note that the average price for an escort pod can be around USD 1.5 M. Such price tags are notably less expensive than the circa USD 125 M publicly available unit price for an E/A-18G.

Credit: Hensoldt
Mission Creep
One of the biggest evolutions expected in the coming years is the addition of cyber effects as part of the jammer’s tactics as discussed above, but other developments are afoot. The doctrine of Multi-Domain Operations (MDO) is being embraced across NATO. MDO strives for the intra- and inter-force connectivity of every warfighter, sensor, weapon, platform and capability at all levels of war to allow synchronous operations across all domains. The goal is to harness and share information to improve the quality and pace of decision making in wartime. High quality, rapid decision-making is seen as vital by NATO if it is to prevail over adversaries in future conflicts.
Professor Steve Roberts, president of the United Kingdom Chapter of the AOC, expects to see a deeper level of connectivity between EW systems in the air domain in the future allowing escort jamming functions to be achieved in new ways. What this could mean in practice is that jammers and Electronic Support Measures (ESMs) on multiple platforms share detailed signal data in real-time allowing geolocation and threat assessment.
Networking these assets could facilitate a more rapid and accurate response to hostile radar threats as and when they appear, with information on hostile emitters moving between blue force airborne EW capabilities at the speed of light.
One example of the potential for future capabilities envisaged by Prof. Roberts is the detection and defeat of a hostile air defence system by CEMA (Cyber and Electromagnetic Activities). The process starts with the detection of RF (Radio Frequency) activity by ESM systems on one or more combat aircraft. The information is immediately shared with other blue force assets supporting an air campaign via secure cloud computing. An escort jammer, many kilometres away from the threatened aircraft acting as a ‘force protection control hub’, receives and integrates this information. Artificial intelligence software recognises the radar activity and intent based on similar waveforms that have been detected in the past. The same software also notes that, based upon past experience, a combination of jamming and insertion of malicious code is likely to be the most effective way to engage this air defence system. The escort jammer shares the appropriate instructions and code with the combat aircraft via the cloud. The EW systems on the threatened aircraft then transmit the appropriate jamming signal. This use of distributed sensors and effectors creates the desired result of forcing the threat to become inoperative or ineffective.
Such capabilities maybe closer than we think. NATO has introduced the Cooperative Electronic Support Measure (CESMO) communications protocol. CESMO lets participating aircraft and naval vessels share radar threat information with each other across existing communications networks. This helps evolve the airborne electronic warfare mission from one which protects individual, or small groups, of aircraft into an overarching, continuous and contiguous mission performed synchronously with other air operations. It is emblematic of the MDO trajectory of electronic warfare and air operations in general.
Escort jamming technology is developing rapidly. The mission is set to be enhanced significantly in the coming years with the advent of cyber effects and deeper connectivity. Customers have an enviable array of products to choose from multiple vendors. What may seem a relatively simple mission is destined to get more complex.
Thomas Withington


