
Ripple effects: Cyber vulnerability at sea
Dr Alix Valenti
In May 2023, Microsoft detected a Chinese malware attack (Volt Typhoon) on US critical infrastructure on the Guam base – a crucial node in US operations in the Pacific. The attack relied on simple techniques and, if undetected, could have resulted in hackers successfully modifying tools and commands. In early 2024, the US successfully carried out a cyberattack on an Iranian (alleged) spy ship, M/V Beshad. Although open-source information on the attack itself is limited, the aim of the attack was clear: to prevent intelligence sharing with Houthi rebels. A source also told the author that a recent analysis of a major navy’s critical ship’s cyber defences revealed that it could paralyse the ship by merely attacking its water supply logistic chain.
These are but three examples of the myriad ways in which cyberattacks can affect a navy. They reveal that adversaries can target any system or platform and, with limited efforts and means, inflict significant damage beyond the hacked system.
As such, addressing a threat with multiple – and potentially unknown – ripple effects requires mobilising several resources. From supply chain and industry leaders to navy strategic thinkers and system operators, “cybersecurity is not just a matter for experts; it’s everyone’s responsibility”, as Patrick Radja, Vice President of Cybersecurity Director at Naval Group, told MDM.

Naval platforms and systems have become significantly digitalised and interconnected over the last ten years. Captain Thomas, Deputy to the Authority responsible for coordinating cybersecurity within the French Navy, explained in an interview with MDM that their goal was to use advancements in new technologies, especially those involving data, to enhance reaction times, facilitate data sharing, and improve maritime situational awareness through sensor data pooling. These sensors can collect data on a ship’s systems for predictive maintenance and asset management as well as gather, analyse, and share information related to situational awareness during missions, including collaborative combat.
However, this increase in digitalisation has also widened the door for potential attacks for adversaries. This issue affects both older platforms that were not designed with cybersecurity in mind and newer, highly digitalised platforms such as the French FDI frigate (Frégate de Défense et d’Intervention). The challenge also extends to the growing use of unmanned aerial, surface, and underwater systems, each having unique constraints. The consequences of a cyberattack disrupting communication links or allowing an adversary to gain control for reverse engineering or data theft are serious.

Several interviewees mentioned that cyber vulnerabilities are not new. “Certain systems inherently have vulnerabilities throughout their lifecycle,” Captain Thomas added. However, the conflict in Ukraine has highlighted the importance of cybersecurity as an established combat domain. Radja stressed that it’s crucial to be aware of the cyber weapon’s ability to neutralise, disrupt, or impair adversary operations or extract classified information directly from weapon systems or supply chains. Therefore, cybersecurity—considering possible vulnerabilities and solutions—must become a fundamental part of operational practices.

Cybersecurity is often thought to begin with the conception of the platform or system—at least today, given interconnectedness. But in practice, it starts much earlier, with the supply chain.
Alain Deturche, Cybersecurity Authority for Thales Defence Mission Systems, explained to MDM that “Primes such as Thales have been working for several years to secure internal production processes,” making it more difficult to hack companies like Thales. He noted, “For hackers, the easiest way to attack a system is to hack a subcontractor.” Several subcontractors are typically involved in developing a system or platform, and not all will have the same levels of cyber maturity and protection. Consequently, an attacker could hack one of the subcontractors, inserting malicious code into the part of the system they are delivering—whether a radar, a communication system, or a SCADA (Supervisory Control and Data Acquisition) system—that has been programmed for activation with specific commands.
Axel Durbec, Technical Project Manager at Exail, reported cases where systems were physically hacked on the production site, with attackers introducing malware that provides remote access to the system once it is operational with the acquiring navy.
Beyond the physical supply chain, prime contractors working with subcontractors also need to monitor potential software supply chain hacks. Systems developed by companies like Thales, Naval Group, L3Harris, or BAE Systems include multiple external software components, requiring complete visibility over the software supply chain. Radja emphasised the need for full traceability and an adequate selection and monitoring process to trust and integrate any software component into their system. This is particularly important for unmanned and autonomous systems. As Durbec noted, installing malware on these systems could affect their capabilities or result in espionage by intercepting valuable, sensitive information.
Ultimately, Mark Keyworth, Cybersecurity Consultant at BMT, told MDM, “It is not just about who these companies are dealing with from a supply company basis; it is also about being able to track the supply chain provenance as far back as where they are getting their supplies from, such as the motherboard, chip, or piece of equipment.”
Vulnerability at sea
“When trying to understand cyber vulnerabilities for naval platforms, whether manned or unmanned, one key element to bear in mind is that these platforms combine very different types of technologies [e.g., SCADA systems, operational technologies, information technology, combat management system, sensors, etc.] and, as such, the result is a very complex architecture,” Deturche explained. Each of these systems will have its own lifecycles and undergo various system updates and upgrades, making it particularly difficult to maintain an up-to-date mapping of all systems and – inevitably – vulnerabilities.
Nevertheless, all interviewees agreed that Operational Technologies (OT) are one of the most significant vulnerabilities on board a naval platform. “Before the digitalisation of the past decade, cybersecurity of OT systems was not a priority because those systems, such as propulsion and turbines, were not connected,” Keyworth said. Yet because many OTs are now connected to onboard platform management systems, sharing information with other systems, it has become critical to understand how the convergence of ITs and OTs creates a gap for cyber attackers to exploit. For instance, by exploiting a vulnerability in a communication network, a hacker could gain access to the propulsion systems and render a ship completely inoperable. Without having to deploy kinetics effects, the ship has been neutralised in its mission.
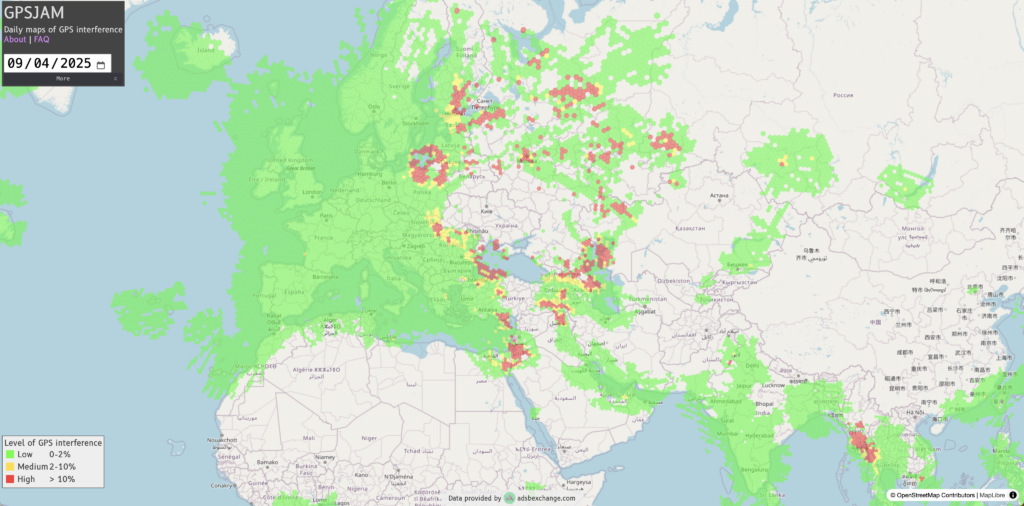
Another significant surface of attack that has emerged over the past few years, especially since the war in Ukraine, is within the electronic warfare (EW) domain. There have been several reports of GPS jamming in the Black Sea, Baltic Sea and Persian Gulf regions, which can create significant disruption. GPS spoofing is also a substantial threat to navy ships. Such attacks can generally be managed in a manned vessel, where the crew can use other systems (such as gyro compass and inertial navigation) to navigate. “Crew onboard may also have emergency response plans to restore a ship’s functions if there are no irreversible impacts on the system, but for unmanned (i.e., human-in-the-loop) and (fully) autonomous systems, which rely on communication systems for several critical functions, restoring functionality after an attack may require recovering the asset,” Durbec explained.
Finally, and as important as any of the physical and software vulnerabilities outlined above, there is the human factor. “There are three main categories of cybersecurity vulnerabilities for a navy,” Captain Thomas explained, “and those are technological, humans operating systems onboard, and humans using other communication systems for recreational purposes.” Most reports published on cyberattacks highlight that in 90% of the cases these attacks were successful due to human error.
High-Level solutions
“Over the past few years, regulations concerning cybersecurity have evolved to meet some of the main challenges the naval industry faces at all levels,” Radja noted. Legislative frameworks like the European NIS-2 directive and IACS Unified Requirements have increased awareness among stakeholders. The French Navy’s cybersecurity strategy, Navy Cyber Ambition 2030, outlines three strategic objectives: digital security, innovative cyber defence, and cyber intelligence.
“We see a positive impact on client awareness and demand for cyber resilience,” Radja explained, “fostering collective action.” Captain Thomas added that the new framework helps armed forces manage cyber threats and maintain operational freedom.
As is often the case, regulatory progress remains slow, which subsequently can also slow down, or even hinder, innovation. Take USVs (unmanned surface vehicles) as an example. As they can potentially navigate in busy waters, they are subject to COLREG (Collision Regulations) to ensure safety of navigation. This delays certification processes. “Where industry will work to ensure cybersecurity maintenance, making regular real-time adjustments to meet emerging threats, the complex safety certification process prevents easy and regular updates,” Deturche explained.

Industry solutions
“Every cybersecurity study begins with a risk assessment,” Durbec explained, “and this risk estimation drives the measures put in place to mitigate them.” This sentiment was echoed by all interviewees for this article.
Risk analysis entails understanding not only the system itself – its surface of attack and potential security gaps – but also the context in which it will operate, the types of missions it will carry out (will it be used to monitor critical infrastructure or on intelligence, surveillance and reconnaissance (ISR) missions off a potential adversaries’ coast), and which potential adversary it will encounter. This analysis will subsequently inform the intrinsic cybersecurity quality of the system that will be delivered to the customer, but it is not enough. It needs to be complemented with extensive exchanges with customers to understand the right balance between the level of acceptance for certain risks versus mission criticality. “We often support customers balance strict cyber strategies with operators’ evolving mission needs,” added Durbec.

In addition to collaborating on risk analyses that guide the development of cybersecure platforms and systems, some companies maintain their own CERT (Computer Emergency Response Team), such as Naval Group, or equivalent industry actors. Similar to the DEFNET wargaming event, the CERT conducts scenario planning to assess potential risks and devise effective solutions. Ultimately, as Deturche explained, “It is all about having the relevant expertise to be able to have the right risk analysis and the right solution for each specific need and constraint.”
These exercises extend to cyber-risk analysis and security within the supply chain. “Continuous web teaming, cyber wargaming and simulating defensive cyber-operations are critical to introducing resilience in the supply chain but also to ensuring that there is rapid incident response,” Keyworth noted. It is about training people and ensuring they understand the stakes rather than merely seeking to comply with cybersecurity rules. “Successful training leads to people operating and maintaining their equipment in a cyber secure manner,” Radja commented, “whereas mere compliance is inefficient.” To this end, large companies such as Naval Group and Thales will also work closely with their subcontractors and suppliers to train their employees.
Cybersecurity at Sea
Captain Thomas told MDM that the French Navy addressed technology-related cybersecurity issues in four ways.
The first approach is cybersecurity by design. As emphasised by industry leaders interviewed for this article, this is a critical step, with the French Navy adhering to its own cybersecurity requirements in addition to European and IACS standards. Captain Thomas elaborated: “For certain types of ships, such as submarines and surface ships, there are specific documents issued by the DGA (Direction Générale de l’Armement) which outline cybersecurity requirements tailored to the operational contexts of these vessels.”
The second approach involves cybersecurity maintenance (Maintient en Conditions de Sécurité – MCS). Analogous to In-Service support, MCS focuses on the continuous management of identified vulnerabilities within a contractual framework. Captain Thomas further clarified, “It also encompasses all the skills necessary for the crew to effectively address a cyber incident.”
The third approach is cyber surveillance, which entails the ongoing monitoring of all systems to identify potential cybersecurity incidents and attacks. This function is performed by the Security Operations Centre and relies on detection rules that enable operators to recognise anomalies in system operations and determine whether they signify a cyberattack or a false positive.
The fourth approach, consistent with industry practices, is the accreditation of an information system. This process aims to deliver a formal decision on the system’s authorisation to operate based on the desired security level and acceptable residual risks. In the military context, this command-level decision is informed by system use descriptions, threat assessments, risk analyses, technical studies, and penetration testing. Captain Thomas noted, “On this basis, we define the level of risk we are prepared to accept for our systems.”
At the organisational level, the French Navy incorporates information system security specialists, operational cybersecurity specialists, and cybersecurity experts across all commands. Additionally, the Cyber Defence Support Centre undertakes three specific missions: training crews to respond to cyber incidents (including through DEFNET and E=MC2 wargaming exercises), constant network monitoring to detect incidents and attacks, and intervention in the event of a cyberattack.

The autonomy cyber conundrum
The increasing integration of artificial intelligence (AI) in navy systems to support decision-making and enable autonomous systems will bring new cybersecurity challenges in the near future.
One key challenge will be ensuring the integrity of the data used to train AI algorithms, noted Lambert. Data poisoning, which involves injecting incorrect information into the training algorithm, could impair a system’s capabilities, such as causing a radar to fail to recognise certain targets, or provide inaccurate decision-making scenarios to an autonomous system.
To mitigate such risks, it will be important to ensure data integrity and develop explainable AI models, according to Captain Thomas. Thales has initiated cortAIx, an AI accelerator aimed at enhancing the integration of AI technology across all sectors of the company, including defence. Deturche highlighted that despite these efforts, some AI models may still be susceptible to attacks or data poisoning, making behavioural analysis crucial for detecting cyberattacks against AI-enabled systems. Behavioural analysis involves comparing an AI system’s actions with its expected behaviour to identify inconsistencies.
In the long term, several navies may adopt ‘zero trust’ architecture for their OT, IT, and C4ISR systems, as indicated by Lambert. This approach is primarily driven by the US Navy and NATO. “This is the ultimate in-depth defence concept, and navies will have to integrate it into their thinking because it will be critical for interoperability,” Captain Thomas concluded.

Author: Dr Alix Valenti is a freelance defence journalist with 10 years’ experience writing about naval technologies and procurement. From 2017 to 2019, she was Editor-in-Chief of Naval Forces. Alix holds a PhD in post-conflict reconstruction.





